
Chairman DeGette, Ranking Member Griffith and Members of the Subcommittee, my name is Kemba Walden, and I am an Assistant General Counsel in Microsoft’s Digital Crimes Unit (“DCU”), where I lead our Ransomware Analysis and Disruption Program. I am also the co-chair of the Disruption working group of the Institute for Security and Technology (IST) Ransomware Task Force, which brings together experts across industries to combat the threat of ransomware.[1] Prior to Microsoft, I spent a decade in government service at the U.S. Department of Homeland Security. At DHS, I held several attorney roles, specifically as the lead attorney for the DHS representative to the Committee on Foreign Investment in the United States and then as a cybersecurity attorney for the Cybersecurity and Infrastructure Security Agency, and its predecessor. I want to thank you for the opportunity to discuss ransomware attacks and illustrate why increased and meaningful information-sharing and public private partnerships are critical to combatting this latest virulent example of costly cybercrime.
I’m also pleased to share information about how Microsoft is combatting ransomware. We believe the best strategy to decrease ransomware attacks is through targeted disruption campaigns along with increased cyber security hygiene. I will close by highlighting several key opportunities for more effective disruption of this cybercrime, opportunities to raise the collective security of public sector and private sector organizations, and the importance of partnerships.
Ransomware attacks pose an increased danger to all Americans as critical infrastructure owners and operators, small and medium businesses, and state and local governments are targeted by sophisticated criminal enterprises and nation-state proxies, operated by distinct criminal organizations. A sustainable and successful effort against this threat will thus require a whole-of –government strategy executed in close partnership with the private sector.
I. Microsoft’s Approach to Cybercrime
Microsoft plays offense against online threats. Working through robust partnerships, we strive to take down criminal infrastructure and pursue both financially motivated and nation state supported cybercriminals. This work helps us to protect our customers and to improve the safety of the global internet community so that all users – enterprises, consumers, and governments – can trust the technology and online services on which we rely for commerce and communication. The Microsoft Digital Crimes Unit (DCU) is an international team of technical, legal, and business experts that has been fighting cybercrime to protect victims since 2008. We use our expertise and unique view into online criminal networks to act. We share insights internally that translate to security product features, we uncover evidence so that we can make criminal referrals to appropriate law enforcement throughout the world, and we take legal action to disrupt malicious activity.
As part of the DCU, Microsoft’s new Ransomware Analysis and Disruption Program, which we launched in 2020, strives to make ransomware less profitable and more difficult to deploy by disrupting infrastructure and payment systems that enable ransomware attacks and by preventing criminals from using Microsoft products and services to attack our customers. The program is based on Microsoft’s decade-long experience and history of success driving a sustained fight against other types of cybercrime.
In addition to partnering with law enforcement to disrupt cybercriminals involved in ransomware attacks, such as the recent disruption of the payment system of the cybercriminals that attacked Colonial Pipeline, Microsoft also uses our expertise to inform cybercrime legislation and global cooperation that advances the fight against cybercrime. We provided substantial support to IST and participated in all four working groups of the Ransomware Task Force. I personally co-chaired the Task Force’s Disruption working group. My colleagues and I are also active participants in the World Economic Forum’s Partnership Against Cybercrime, focused on global policy efforts to combat ransomware.
Through Microsoft’s observations of ransomware deployment and attacks, our active collaboration with the U.S. Government to date, and Microsoft’s thought leadership in the global discussion on policy and operational opportunities to counter ransomware, I will next address opportunities for more effective disruption of this cybercrime, opportunities to raise the collective security of public sector and private sector organizations, and the importance of partnerships.
II. Defining Ransomware
A. What is a Ransomware Attack?
Ransomware is a specific kind of malicious software or “malware” used by cybercriminals to render data or systems inaccessible for the purposes of extortion – i.e., ransom. In a standard ransomware attack the cybercriminal achieves unauthorized access to a victim’s network, installs the ransomware, usually in locations with sensitive data or business critical systems, and then executes the program, locking files on that network, making them inaccessible to the victim until a ransom is paid. Usually, the ransom demand is for payment in the form of cryptocurrency – such as Bitcoin. Increasingly, attackers also steal sensitive data before deploying the actual ransomware in what is known as a double extortion ransomware attack. The theft of data compels the victim to engage in negotiations and raises the potential reputational, financial, and legal costs of not paying the ransom as the attackers will not only leave the victim’s data locked, but also leak sensitive information that could include confidential business data or personally identifiable information.
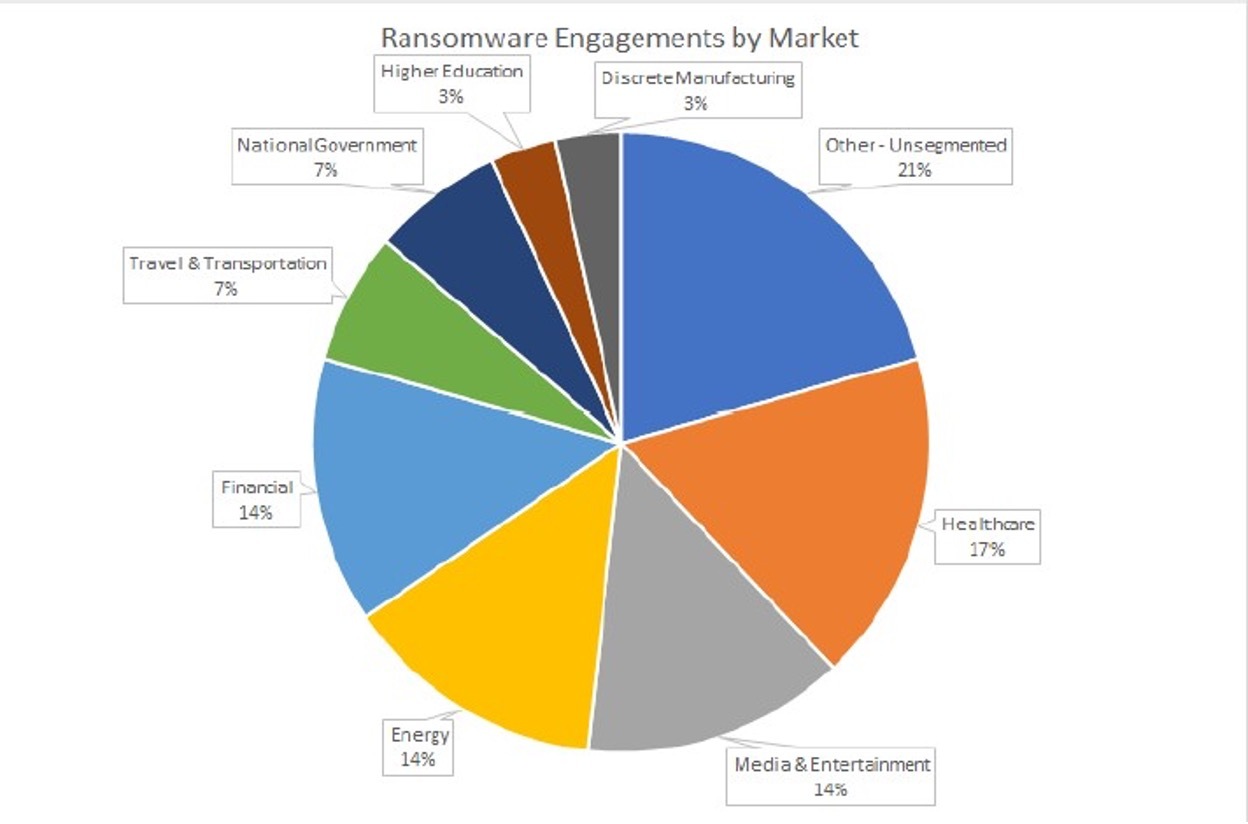
Recent, high-profile incidents such as those involving the Colonial Pipeline, JBS Foods, and Kaseya ransomware attacks drew considerable public attention and illustrate the extent of the threat and the significant, multimillion dollar consequences of ransomware. However, based on Microsoft’s data, ransomware is not limited to high-profile incidents. It is ubiquitous and pervasive, impacting wide swathes of our economy, from the biggest to the smallest players. Our data shows that the energy sector represents one of the most targeted sectors, along with the financial, healthcare, and entertainment sectors. And despite continued promises by some cybercriminals not to attack hospitals or healthcare companies during the global pandemic, Microsoft has observed that healthcare remains the number one target of ransomware.
B. How does a ransomware attack work?
The image below depicts the basic steps that typically take place before a cybercriminal installs the malicious ransomware on a victim’s network. First, cybercriminals will gain access to the victim’s network through phishing, a stolen password, or through an unpatched software vulnerability. Then, the cybercriminals will seek to move laterally within the network to obtain higher level privileges, such as those held by the victim’s IT Administrator, to access the entire network. Cybercriminals will then conduct reconnaissance within the victim’s network, looking for critical systems and sensitive data, in some cases stealing this data, to facilitate an effective ransom demand. Finally, the cybercriminals will leverage this information to install the ransomware on the network that will lock the victim’s files until the ransom is paid.
Read the full article by Microsoft, here: https://blogs.microsoft.com/on-the-issues/2021/07/20/the-growing-threat-of-ransomware/
Phone: (305) 517 1000
Support: (305) 517 1001
Email: [email protected]
LogixCare LLC. 2023 © All Rights Reserved