How many IoT devices are used at your company? If yours is like most organizations, there are probably printers, scanners, and fax machines scattered around the office. Perhaps smart TVs are mounted at reception or in the break room to guide visitors and keep employees up-to-date on company events and news. Or maybe highly connected conference systems bring teams together to collaborate. For some organizations, IoT also includes operational technology (OT) devices used in industrial systems and critical infrastructure. You and your employees probably view these devices as tools to help operate more efficiently. Unfortunately, so do cybercriminals.
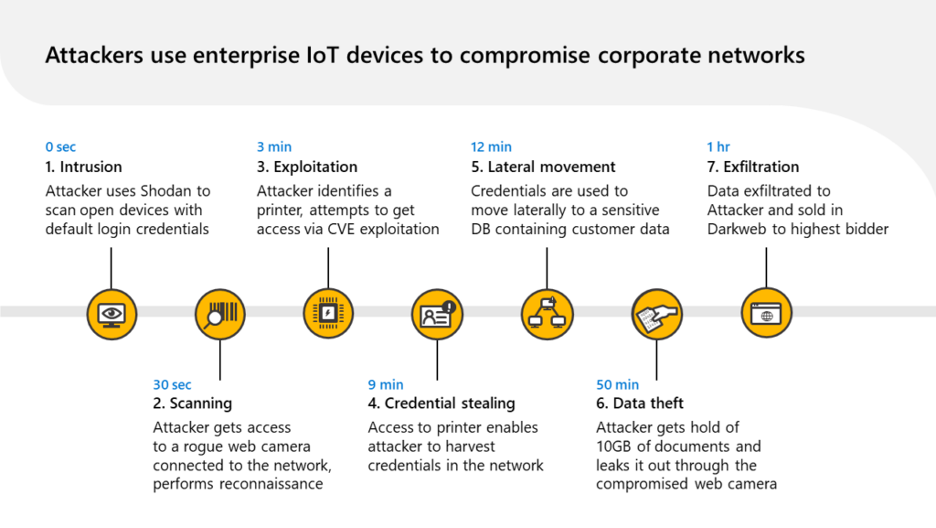
While IoT devices can easily outnumber managed endpoints like laptops and mobile phones, they often lack the same safeguards that would ensure their security. To bad actors, these unmanaged devices can be used as a point of entry, for lateral movement, or evasion. The chart below showcases a typical attack lifecycle involving two IoT devices, where one is used as a point of entry, and another one for lateral movement. Too often, the use of such tactics leads to the exfiltration of sensitive information.
Introducing protection for Enterprise IoT devices in Microsoft Defender for IoT
At the 2021 Microsoft Ignite, we announced the preview of enterprise IoT security capabilities in Microsoft Defender for IoT. With these new capabilities, Defender for IoT adds agentless monitoring to secure enterprise IoT devices connected to IT networks, like Voice over Internet Protocol (VoIP), printers, and smart TVs. A dedicated integration with Microsoft 365 Defender allows Defender for Endpoint customers to extend their extended detection and response (XDR) coverage to include IoT devices. Today, we’re excited to announce the general availability of these capabilities in Defender for IoT.
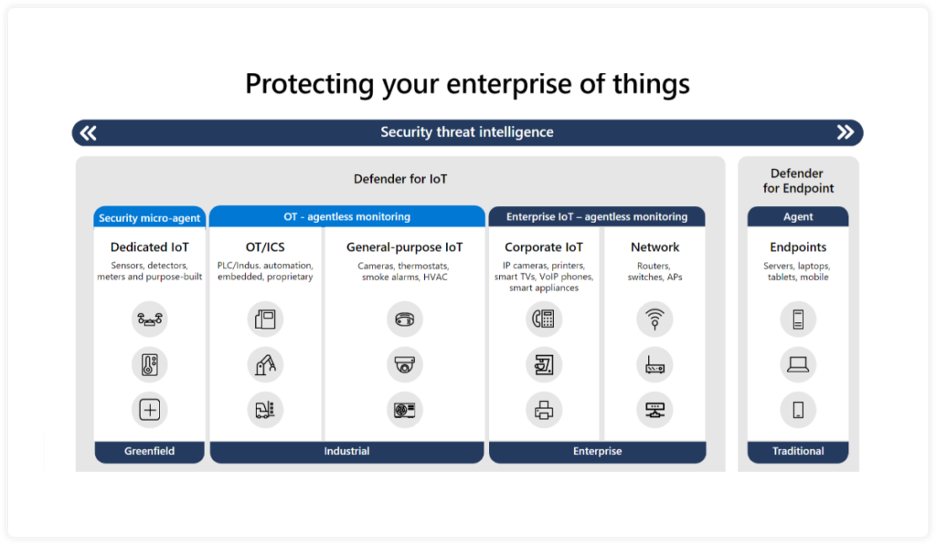
With this new addition, Defender for IoT now delivers comprehensive security for all endpoint types, applications, identities, and operating systems. The new capabilities allow organizations to get the visibility and insights they need to address complex multi-stage attacks that specifically take advantage of IoT and OT devices to achieve their goals. Customers will now be able to get the same types of vulnerability management, threat detection, response, and other capabilities for enterprise IoT devices that were previously only available for managed endpoints and OT devices.
Further, to make Enterprise IoT security accessible to more customers, we are introducing a dedicated native integration for Microsoft 365 Defender customers. The new integration helps customers to discover and secure IoT devices within Microsoft 365 Defender environments in minutes.
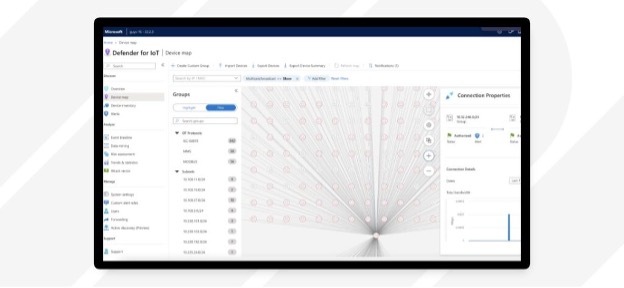
Identifying unmanaged devices
You can’t secure a device if you don’t know it exists. Taking a thorough inventory of all IoT devices can be expensive, challenging, and time-consuming. Employees may connect IoT devices to the network without first notifying IT or operations.
By using the existing Microsoft Defender for Endpoint clients, which are often deployed pervasively across an organization’s infrastructure, we can provide immediate device discovery with no additional deployment or configuration required. For the most complete view of your IoT and OT devices, and specifically for network segments where Defender for Endpoint sensors are not present, Defender for IoT includes a deployable network sensor that can be used to collect all of the network data it needs for discovery, behavioral analytics, and machine learning.
Understanding device vulnerabilities
Knowing all the devices present in your network is a critical step to securing your IoT—but it’s only the first step. To understand the potential risk that those devices pose to your network and organization, you need to be able to stay on top of insecure configurations and vulnerabilities that may be present within your inventory of devices.
These types of devices are often unpatched, misconfigured, and unmonitored, which makes them an immediate target for an attacker. Defender for IoT assesses all your enterprise IoT devices, offering recommendations in the Microsoft 365 console as part of the ongoing investigation flow for network-based alerts.
New IoT devices are being introduced into an environment all the time. Because of that, the identification and risk assessment processes run continuously within Defender for IoT to ensure maximum visibility and posture at all times.
Read the full article by Microsoft: https://www.microsoft.com/security/blog/2022/07/11/introducing-security-for-unmanaged-devices-in-the-enterprise-network-with-microsoft-defender-for-iot/
Visit our website: https://logixcare.com/blog
