
As businesses around the world grapple with the growth of an industrialized, organized attacker ecosystem, the need for customers to secure multicloud and hybrid infrastructure and workloads is increasingly urgent.
Today, organizations face an attacker ecosystem that is highly economically motivated to exploit security issues with your multicloud and hybrid workloads—as made evident in the rise in human-operated ransomware, with hackers launching an average of 50 million password attacks every day (579 per second), the rise of web shell attacks, and increasing firmware attacks. As with most attack vectors in this evolving threat landscape, prevention and detection are critical.
These threats can present a growing challenge for organizations using a combination of on-premises, hybrid, and multicloud infrastructure and workloads. With this distributed infrastructure, it can be a challenge to protect resources against motivated attackers when security management, policies, and signals are not unified.
Securing your multicloud and hybrid infrastructure in 3 steps:
Securing infrastructure is fundamental to the business—for every business. So, what does a solution for multicloud, on-premises, and hybrid infrastructure security look like? A powerful defense must be unified, simplified, and actionable. It must make it easier to enable digital transformation and not slow progress in this crucial area. For businesses who need to secure multicloud, on-premises, and hybrid infrastructure, an increased security stance can start with three simple steps:
1. Connect your on-premises and hybrid infrastructure to Microsoft security services using Azure Arc
Many organizations today are challenged with the growing complexity of securing their infrastructure with disparate tools across multicloud, hybrid, and edge environments. To begin securing these assets, you can use Azure Arc to connect your resources to Microsoft Azure from wherever they are deployed, making them addressable by Azure security services and enabling you to manage them from a single pane of glass in Azure Resource Manager. Azure Arc extends the control plane to these resources so that they can be managed and secured centrally with tools including our cloud extended detection and response (XDR) solution, Microsoft Defender for Cloud, or the secure key management tool, Azure Key Vault.
2. Secure your Azure Arc-enabled infrastructure using Microsoft Defender for Cloud
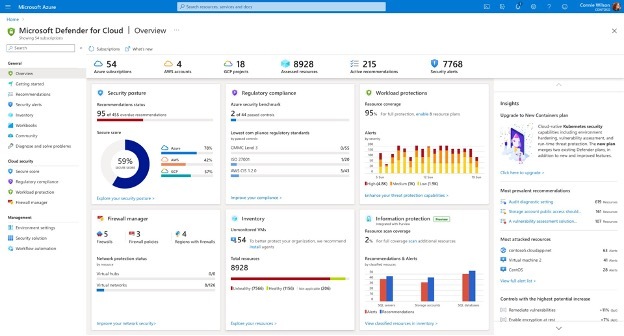
Once these distributed multicloud and hybrid environments are connected through Azure Arc, Microsoft Defender for Cloud enables you to find weak spots across your configuration, helps strengthen the overall security posture, and can help you meet any relevant compliance requirements for your resources across Azure, Amazon Web Services (AWS), and Google Cloud Platform (GCP).
While prevention is critical, at the same time, the increasing sophistication of attacks requires that organizations have a comprehensive threat protection strategy in place. Microsoft Defender for Cloud provides vulnerability assessment with insights from industry-leading security research and provides advanced threat protection for a broad range of workloads across cloud and on-premises including virtual machines, containers, databases, storage, and more.
Get started by enabling Microsoft Defender for Cloud for your Azure subscriptions and easily onboard other environments to understand your current security posture. You can then enable the enhanced features to protect and manage the security of all relevant workloads across your cloud and on-premises environments from a central place, all connected through Azure Arc.
3. Further secure your on-premises and hybrid infrastructure using Secured-core for Azure Stack HCI
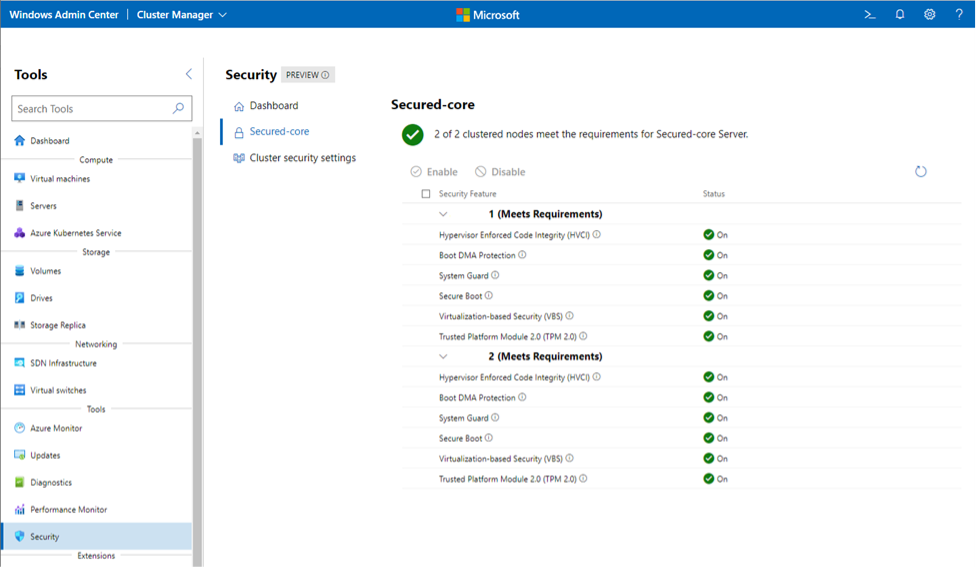
As security threats continue to become more sophisticated, they are moving lower in the stack to the operating system, firmware, and hardware level, so there is a growing need for additional security at these lower levels. One way to gain additional protection against these attacks is an integrated solution called Secured-core, now available for Azure Stack HCI. Secured-core servers provide out-of-box safeguards with enhanced protections. For example, Secured-core servers help stop attacks in the event of a successful web application compromise with features like virtualization-based security (VBS) and hypervisor-based code integrity (HVCI). Credential protection in Azure Stack HCI helps mitigate the common attack of credential theft by using VBS to isolate credentials in their own virtual machine, a feature that is on by default in Secured-core servers. These features help prevent what could otherwise be a much larger breach.
Secured-core servers have three focused pillars:
All these capabilities built into Secured-core servers ensure that your servers are protected out-of-box, giving you confidence in your hardware. And managing the status and configuration of Secured-core servers is easy from the browser-based Windows Admin Center for both Windows Server and Azure Stack HCI solutions.
Read the complete blog by Microsoft and subscribe to our blog to keep up with our expert coverage on security matters. Also, follow us at @logixcare for the latest news and updates on cybersecurity.
Phone: (305) 517 1000
Support: (305) 517 1001
Email: [email protected]
LogixCare LLC. 2023 © All Rights Reserved